
Matt
-
Content Count
3352 -
Joined
-
Last visited
Content Type
Profiles
Forums
Calendar
Posts posted by Matt
-
-
For assistance with malware, please read How To Post An OTL Log in the Malware Removal Forum.
-
I guess the Yahoo Search box in firefox will soon switch to bing then.
But since I only ever use the Google, YouTube, and Wikipedia searches.... it doesn't bother me
-
Happy birthday man!
Geez... half way to 40... haha
-
I'd just let the Congressional Judiciary Committee handle it. Sure, the DoJ would pretty much have to get involved. I'd rather see action than looking the other way.Obama, on the other hand, is in a predicament: if he takes action against Cheney or any former CIA officials, he'll be compromising his (apparent) belief that we should put the Bush years behind us and move on, and setting a precedent that could come back to haunt him. On the other hand, if he doesn't take action he looks like he condones, or even supports, Cheney's behavior.
I dont think Cheney and Clinton fell into the same category.I thought we learned ten years ago that symbolic impeachments are a bad idea. -
Cheney, however, has not kept his mouth shut, and I think they'll be finding anything and everything to throw at him, to punish him for speaking his mind. They have a target and they'll be aiming for it.
Or they're finding out more and more illegal things Cheney did that should have gotten him impeached back when Kucinich was pushing for it.
-
Telling folks in Congress what's going only gives them reason to hold chest thumping hearings, fly off on junkets or share the info with their pillow mates, whomever it is at the time.They have to be briefed or it's illegal.
No one obeys these laws and no one expects them to be obeyed. I mean, Christ, if this story is accurate, we only know that this program exists because someone leaked the contents of a classified briefing to the NYT.
Even still, the point isn't whether or not "anyone obeys these laws", or if it is necessary. The point is that they didn't obey it, info got out, and now its a problem. If the law is impractical, then they should change the law. Until then, if they're gonna risk something like this they have to be willing for this kind of result.
-
Congress has NEVER been fully informed. That would kind of defeat the purpose of the CIA (and all the other acronyms).
Doesn't matter. They have to be briefed. National Security Act of 1947
SEC. 501. [50 U.S.C. 413] (a)(1) The President shall ensure that the congressional intelligence committees are kept fully and currently informed of the intelligence activities of the United States, including any significant anticipated intelligence activity as required by this title.I'm not sure I trust Congress anyway.
Doesn't matter if you trust them. They have to be briefed or it's illegal.(e) Nothing in this Act shall be construed as authority to withhold information from the congressional intelligence committees on the grounds that providing the information to the congressional intelligence committees would constitute the unauthorized disclosure of classified information or information relating to intelligence sources and methods. -
Inactive topic...
If you still need help on this problem, contact me or one of the Moderators to re-open this up.
Topic closed.
-
Inactive topic...
If you still need help on this problem, contact me or one of the Moderators to re-open this up.
Topic closed.
-
For assistance with malware, please read How To Post An OTL Log in the Malware Removal Forum.
-
Hi and welcome to BestTechie! I'll be assisting you to clean up your computer. The first thing I need you to do is follow the steps in this thread. Make sure you go through all of the procedures, and post back here with the logs you get back.
-
beaners,
Would you mind clarifying what this is about?
Matt
-
Inactive topic...
If you still need help on this problem, contact me or one of the Moderators to re-open this up.
Topic closed.
-
Hi causey, and welcome to BestTechie! I'll be assisting you to clean up your computer. The first thing I need you to do is follow the steps in this thread. Make sure you go through all of the procedures, and post back here with the logs you get back.
Matt
-
Welcome to Vista! How do you like it? Not quite as bad as people make it out to be, eh?
Most of the stuff I was looking for I either figured out or will eventually (I PREFER, for example, to have file extensions displayed, but it's not a high priority).Did you find how to do this?
1. Open a folder or open explorer
2. Click the Layout button (to the left of the Views button)
3. Click Folder Options
4. Click the View tab
5. Uncheck Hide extensions for known file types
6. Click OK
-
SystemRescueCD is a life saver. I love it.
-
Something I saw on Flickr:
-
Since this issue appears to be resolved ... this Topic has been closed. Glad we could help.

If you're the topic starter, and need this topic reopened, please contact a staff member with the address of the thread.
Everyone else please begin a New Topic.
-
I love PHP. Was my first step into programming (even though it's technically a scripting language). Thanks for the info!

-
Everything looks good!
Now we need to create a new System Restore point.
Click Start Menu > Run > type (or copy and paste)
%SystemRoot%\System32\restore\rstrui.exe
Press OK. Choose Create a Restore Point then click Next. Name it and click Create, when the confirmation screen shows the restore point has been created click Close.
Next goto Start Menu > Run > type
cleanmgr
Click OK, Disk Cleanup will open and start calculating the amount of space that can be freed, Once thats finished it will open the Disk Cleanup options screen, click the More Options tab then click Clean up on the system restore area and choose Yes at the confirmation window which will remove all the restore points except the one we just created.
To close Disk Cleanup and remove the Temporary Internet Files detected in the initial scan click OK then choose Yes on the confirmation window.
- Download OTCleanIt to your desktop and run it
- Click Yes to beginning the Cleanup process and remove these components, including this application.
- You will be asked to reboot the machine to finish the Cleanup process. Choose Yes.
Your using an old version of Adobe Acrobat Reader, this can leave your pc open to vulnerabilities, you can update it here :
http://www.adobe.com/products/acrobat/readstep2.html
Please download JavaRa to your desktop and unzip it to its own folder
- Run JavaRa.exe, pick the language of your choice and click Select. Then click Remove Older Versions.
- Accept any prompts.
- Open JavaRa.exe again and select Search For Updates.
- Select Update Using Sun Java's Website then click Search and click on the Open Webpage button. Download and install the latest Java Runtime Environment (JRE) version for your computer.
Below I have included a number of recommendations for how to protect your computer against malware infections.
- Keep Windows updated by regularly checking their website at :
http://windowsupdate.microsoft.com/
This will ensure your computer has always the latest security updates available installed on your computer. - SpywareBlaster protects against bad ActiveX, it immunizes your PC against them.
- SpywareGuard offers realtime protection from spyware installation attempts. Make sure you are only running one real-time anti-spyware protection program ( eg : TeaTimer, Windows Defender ) or there will be a conflict.
- Make Internet Explorer more secure
- Click Start > Run
- Type Inetcpl.cpl & click OK
- Click on the Security tab
- Click Reset all zones to default level
- Make sure the Internet Zone is selected & Click Custom level
- In the ActiveX section, set the first two options ("Download signed and unsigned ActiveX controls) to "Prompt", and ("Initialize and Script ActiveX controls not marked as safe") to "Disable".
- Next Click OK, then Apply button and then OK to exit the Internet Properties page.
[*]ATF Cleaner - Cleans temporary files from IE and Windows, empties the recycle bin and more. Great tool to help speed up your computer and knock out those nasties that like to reside in the temp folders.
[*]MVPS Hosts file replaces your current HOSTS file with one containing well known ad sites and other bad sites. Basically, this prevents your computer from connecting to those sites by redirecting them to 127.0.0.1 which is your local computer, meaning it will be difficult to infect yourself in the future.
[*]Please consider using an alternate browser. Mozilla's Firefox browser is fantastic; it is much more
secure than Internet Explorer, immune to almost all known browser hijackers, and also has the best built-in pop up
blocker (as an added benefit!) that I have ever seen. If you are interested, Firefox may be downloaded from
If you choose to use Firefox, I highly recommend these add-ons to keep your PC even more secure.
- NoScript - for blocking ads and other potential website attacks
- McAfee SiteAdvisor - this tells you whether the sites you are about to visit are safe or not. A must if you do a lot of Googling
[*]Keep a backup of your important files - Now, more than ever, it's especially important to protect your digital files and memories. This article is full of good information on alternatives for home backup solutions.
[*]ERUNT (Emergency Recovery Utility NT) allows you to keep a complete backup of your registry and restore it when needed. The standard registry backup options that come with Windows back up most of the registry but not all of it. ERUNT however creates a complete backup set, including the Security hive and user related sections. ERUNT is easy to use and since it creates a full backup, there are no options or choices other than to select the location of the backup files. The backup set includes a small executable that will launch the registry restore if needed.
[*] Recovery Console - Recent trends appear to indicate that future infections will include attacks to the boot sector of the computer. The installation of the Recovery Console in the computer will be our only defense against this threat. For more information and steps to install the Recovery Console see This Article. Should you need assistance in installing the Recovery Console, please do not hesitate to ask.
[*]FileHippo Update Checker is an extremely helpful program that will tell you which of your programs need to be updated. Its important to keep programs up to date so that malware doesn't exploit any old security flaws.
[*]Please read my guide on how to prevent malware and about safe computing here
- Click Start > Run
Thank you for your patience, and performing all of the procedures requested.
- Download OTCleanIt to your desktop and run it
-
Download TFC to your desktop
- Open the file and close any other windows.
- It will close all programs itself when run, make sure to let it run uninterrupted.
- Click the Start button to begin the process. The program should not take long to finish its job
- Once its finished it should reboot your machine, if not, do this yourself to ensure a complete clean
Please open Malwarebytes' Anti-Malware.
Under the Update tab, click Check for Updates
- If an update is found, it will download and install the latest version.
- Once done, return to Scanner and select "Perform Quick Scan", then click Scan.
- The scan may take some time to finish,so please be patient.
- When the scan is complete, click OK, then Show Results to view the results.
- Make sure that everything is checked, and click Remove Selected.
- When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.(See Extra Note)
- The log is automatically saved by MBAM and can be viewed by clicking the Logs tab in MBAM.
- Copy&Paste the entire report in your next reply.
Extra Note:
If MBAM encounters a file that is difficult to remove,you will be presented with 1 of 2 prompts,click OK to either and let MBAM proceed with the disinfection process,if asked to restart the computer, please do so immediately.
Then, Go to Kaspersky website and perform an online antivirus scan.
- Read through the requirements and privacy statement and click on Accept button.
- It will start downloading and installing the scanner and virus definitions. You will be prompted to install an application from Kaspersky. Click Run.
- When the downloads have finished, click on Settings.
- Make sure these boxes are checked (ticked). If they are not, please tick them and click on the Save button:
- Spyware, Adware, Dialers, and other potentially dangerous programs
Archives
Mail databases
- Spyware, Adware, Dialers, and other potentially dangerous programs
[*]Click on My Computer under Scan.
[*]Once the scan is complete, it will display the results. Click on View Scan Report.
[*]You will see a list of infected items there. Click on Save Report As....
[*]Save this report to a convenient place. Change the Files of type to Text file (.txt) before clicking on the Save button. Then post it here.
Also, please scan with OTL as you did before and post me an updated log.
So, please post back the MBAM, Kaspersky, and OTL logs.
- Open the file and close any other windows.
-
Re-opened per user request.
-
Way to go man! Nicely done!

-
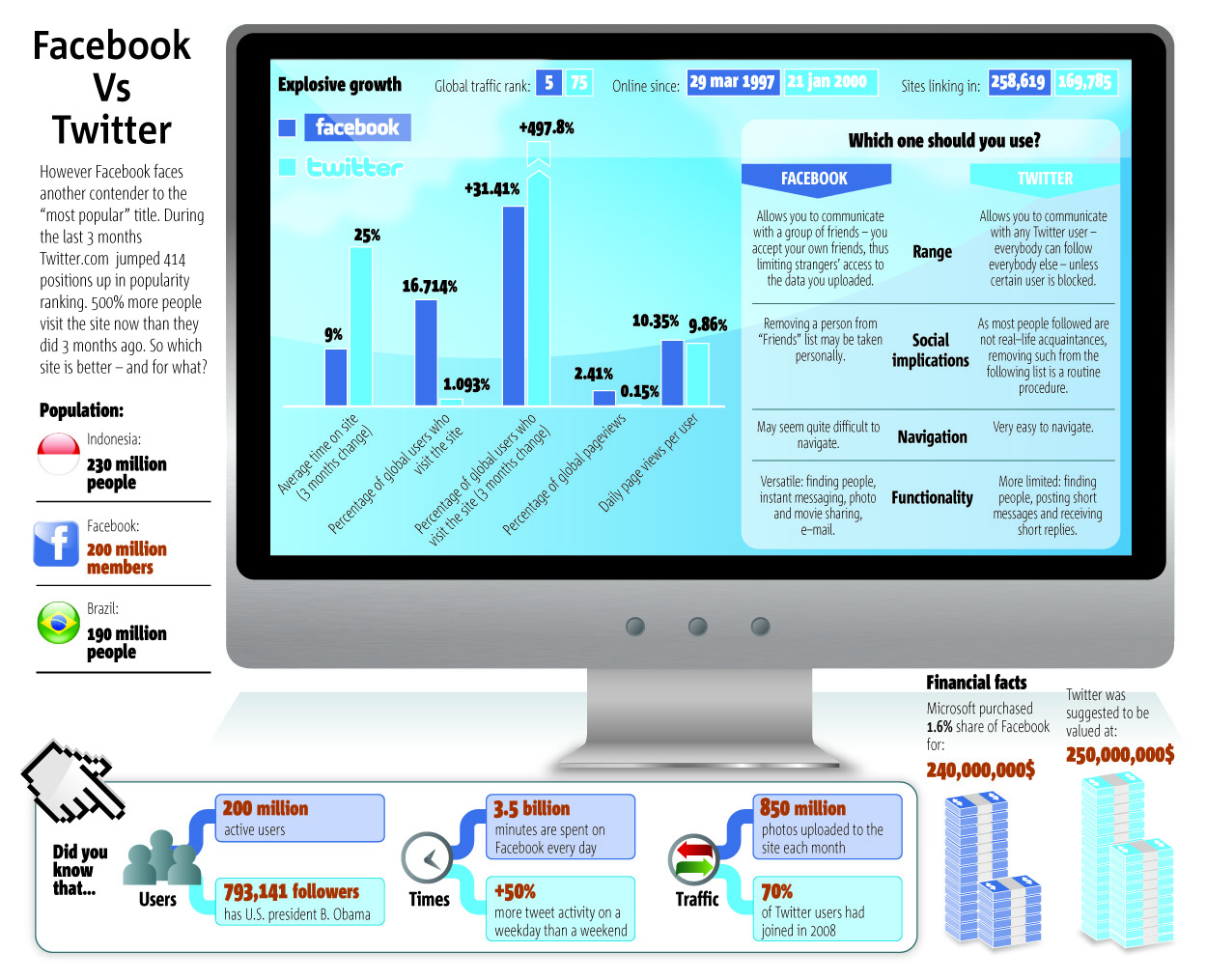
No, I don't use Twitter. I don't plan to use Twitter.
In my opinion, Twitter is only reasonable for celebrities or other public figures. I can understand people wanting to "follow" what Shaq or Obama or Pete Wentz are doing today--and only for the "die hard" fans who need to know everything about that person. Not really for me, but I get why it would appeal to some. However, I don't think anyone cares at all what I ate for breakfast. I think its just a stupid trend.
I also find it ironic that television or internet companies are using twitter. If I want to follow MSNBC, I'm not going to follow them on twitter.com I'm going to follow them on msnbc.com or the MSNBC channel. Same goes for digg, slashdot, cnet, or any other publication.
I think its a fad that will die once people realize "woah, I don't really care what my friend got at McDonalds today." or "hey, RSS feeds from my favorite news source are better than Twitter feeds."

List Of Antivirus Software Not Compatible With Windows 7
in Windows 10, 8, 7, Vista, and XP
Posted
That article is almost 8 months old, and we've moved from Windows 7 Beta to Windows 7 RC. Not very useful info.